Building My Home Lab: A Hands-On Journey into Cybersecurity
Happy Summer Solstice!
Okay, y'all, I have to be honest… this post was drafted back in January as a ‘Happy New Year!' post…🫣
Let me just say, there has been a strong need for slow movement since bringing in 2025, and I’m learning to embrace it.
Feeling focused and refreshed, I’m back on my journey of getting down ‘n dirty with cyber.
So today, let’s talk about how I’ll be setting up my very own virtual home lab.
Wait— what exactly is a virtual home lab?
Think of a home lab as your digital playground, a safe space to experiment, make mistakes, and level up your skills without risking your real-world systems.
Okay, let’s get started!
Step 1: Laying the Foundation
Every great project starts with a vision, and my home lab is no different. I started by setting clear goals to keep myself focused.
My Home Lab Goals:
Gain hands-on experience with cybersecurity tools like Nmap, Metasploit, Wireshark, and Splunk.
Explore different operating systems and their security configurations.
Simulate real-world scenarios, like vulnerability scanning and network traffic analysis.
These goals will help me stay focused and select the right tools and software to meet my needs. Staying intentional and having a vision helps avoid overwhelm and makes the process feel manageable.
Step 2: Setting Up the Virtual Machines
Virtual machines (VMs) will be my go-to because they’re cost-effective, flexible, and perfect for beginners. Before we get deep into the topic, let me explain what VMs and hypervisors are.
🧠 What Is a Virtual Machine (VM)?
A virtual machine (VM) is a software-based simulation of a physical computer. It allows you to run multiple operating systems on a single physical device. Each VM operates in its own isolated environment, which makes it ideal for testing, development, and cybersecurity training.
Why VMs Are Essential in a Cybersecurity Home Lab:
Safe Testing: You can experiment with tools and scenarios without risking your actual system.
Multiple Environments: Run different OSes (Windows, Linux, etc.) side-by-side.
Reusability: Take snapshots to easily roll back after tests or failures.
Scalability: Add more machines as your learning goals evolve.
Whether you’re simulating cyber attacks, running vulnerability scans, or building secure networks, VMs let you build a full virtual infrastructure without needing racks of hardware.
🧠 What Is a Virtual Machine (VM)?
A virtual machine (VM) is a software-based simulation of a physical computer. It allows you to run multiple operating systems on a single physical device. Each VM operates in its own isolated environment, which makes it ideal for testing, development, and cybersecurity training.
Why VMs Are Essential in a Cybersecurity Home Lab:
Safe Testing: You can experiment with tools and scenarios without risking your actual system.
Multiple Environments: Run different OSes (Windows, Linux, etc.) side-by-side.
Reusability: Take snapshots to easily roll back after tests or failures.
Scalability: Add more machines as your learning goals evolve.
Whether you’re simulating cyber attacks, running vulnerability scans, or building secure networks, VMs let you build a full virtual infrastructure without needing racks of hardware.
🧱 What Is a Hypervisor?
A hypervisor is the software layer that allows you to create and run virtual machines on your physical device. It acts as a manager, allocating resources (CPU, memory, storage) from your actual hardware to each VM.
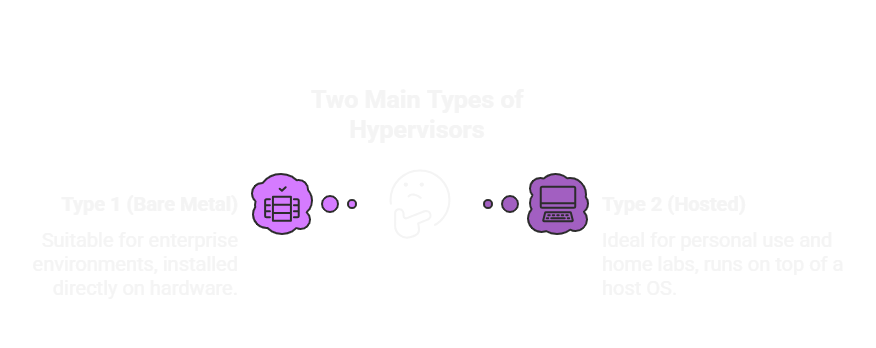
There are two main types of hypervisors:
Type 1 (Bare Metal): Installed directly on hardware (e.g., VMware ESXi). Used in enterprise environments.
Type 2 (Hosted): Runs on top of a host operating system (e.g., VMware Workstation Pro, VirtualBox). Ideal for personal use and home labs.
In my case, I’m using VMware Workstation Pro, a Type 2 hypervisor, which allows me to easily manage multiple VMs from my laptop.
Ok, here’s how I got started:
Step 1: Installing VMware Workstation Pro
I began by downloading VMware Workstation Pro from Broadcom’s official site. Since Player has been retired as of March 2025, Pro now offers free personal use.
Installation was smooth, and I now have a powerful hypervisor with full snapshot, cloning, and resource management capabilities—perfect for running multiple VMs in parallel.
Quick VM vs. Hypervisor Breakdown:
VM: The virtual computer you run, hosted on your device
Hypervisor: The software layer (like VMware) that manages and runs VMs
My host machine is a laptop with 16GB of RAM and 512GB SSD, which provides enough resources to run multiple VMs without any issues.
Step 2: Downloading and Installing VMs
After installing VMware Workstation Pro, I setup VMs with these three core operating systems.
Windows 10 Developer Edition
I’ll use this for defensive security exercises, log analysis, and Active Directory simulations.
Windows Server 2022 (for Domain Controller setup)
This ISO will be used to build a virtual domain with Active Directory, DNS, and Group Policy.
Kali Linux (Latest Stable)
My main system for offensive security tools, penetration testing, and network discovery.
Use Cases for These VMs in My Lab
Each operating system will play a unique role in my cybersecurity practice:
Windows 10
Acts as a client in my virtual network.
Tools: Sysinternals Suite, Splunk (Free), Event Viewer.
Practice tasks: Log monitoring, endpoint protection, system hardening.
Windows Server (Domain Controller)
Simulates enterprise-level infrastructure.
Key Roles: Active Directory, DNS, Group Policy Management.
Practice tasks: User/role permissions, domain security, event logging.
Kali Linux
Used for penetration testing and red teaming.
Tools: Metasploit, Nmap, Burp Suite, Wireshark.
Practice tasks: Network scanning, exploiting vulnerabilities, password attacks
This lets me control the full VMware environment from my Mac—even if it’s across the house—without needing to export and re-import any VMs.
What’s Next?
Once the ISO downloads are complete, I’ll begin configuring each VM with optimized RAM, CPU, and disk space based on their intended purpose.
From there, I’ll:
Document all installation steps.
Set up custom network configurations.
Start my first hands-on practice projects and log everything in my cybersecurity portfolio.
Why Building a Home Lab Matters
Creating a virtual home lab is one of the most accessible and effective ways to break into the cybersecurity field. You don’t need thousands of dollars in hardware—just your laptop, a hypervisor, and curiosity.
Restarting the goal of building my home lab isn’t just about performance—it’s about precision, documentation, and showing up with clarity in my cybersecurity learning journey.
Okay y’all, that's a lot for one take. Join me in my next post where I break down each VM setup and the tools I’ll be installing on each.
What tools or OS are must-haves in your environment? Let’s swap notes below! ⬇️
until next time,
Kenyatta <3